Microsoft has established itself as a leading player in the tech industry, providing a variety of software solutions that are widely used across the globe. However, the increasing complexity of these systems has led to various security vulnerabilities. Organizations and individual users often face risks from security flaws that could compromise sensitive data and disrupt systems. This article explores some of the recent security gaps identified in Microsoft products, their implications, and steps organizations can take to mitigate these risks.
What are the most common Microsoft security flaws?
Common security flaws in Microsoft products include vulnerabilities in operating systems such as Windows, software such as Microsoft Office, and cloud services like Azure. These flaws often arise due to outdated software, misconfigurations, or unpatched vulnerabilities. Attackers exploit these gaps to gain unauthorized access, disrupt services, or steal data.
Recent Vulnerabilities and Their Impact
In recent months, Microsoft has reported several high-profile vulnerabilities, prompting businesses and users alike to reassess their security postures. Here are some notable instances:
1. Windows Print Spooler Vulnerability
Discovered in mid-2021, this vulnerability, referred to as “PrintNightmare,” allows attackers to execute arbitrary code with elevated privileges. Security researchers identified that by exploiting vulnerabilities in the Print Spooler service, attackers could install programs, view or delete data, and create new user accounts with full rights.
- Severity Level: Critical
- CVSS Score: 8.8
2. Microsoft Exchange Server Vulnerabilities
Microsoft Exchange Server has faced several vulnerabilities this year, notably the “ProxyLogon” exploits. These flaws permit attackers to bypass authentication and run arbitrary code on vulnerable servers. The implications include potential data exfiltration and unauthorized access to enterprise networks.
- Severity Level: High
- CVSS Score: 9.8
Implications for Organizations
The repercussions of these vulnerabilities can be severe. Organizations may face financial losses, legal consequences, and a damaged reputation. A recent report from Cybersecurity Ventures estimates that global cybercrime damages will hit $10.5 trillion annually by 2025, emphasizing that the stakes are higher than ever.
To illustrate these findings, consider the following table showing the estimated costs associated with data breaches over the past few years:
| Year | Average Cost of Data Breach (USD) | Total Number of Data Breaches |
|---|---|---|
| 2019 | 3.92 million | 11.7 billion |
| 2020 | 3.86 million | 9.8 billion |
| 2021 | 4.24 million | 14.9 billion |
Strategies for Mitigating Risks
Organizations must adopt comprehensive strategies to protect against these vulnerabilities. Below are several proactive steps:
Regular Software Updates
Keeping software up-to-date is critical. Microsoft routinely issues patches and updates aimed at fixing known vulnerabilities. Organizations should implement an update management process to ensure timely installation.
Employee Training
Human error remains a significant factor in cybersecurity breaches. Conducting regular training can help employees recognize phishing attempts and other attacks that exploit security flaws.
Implementing Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring two or more verification factors to gain access to an account. This practice significantly reduces the risk of unauthorized access.
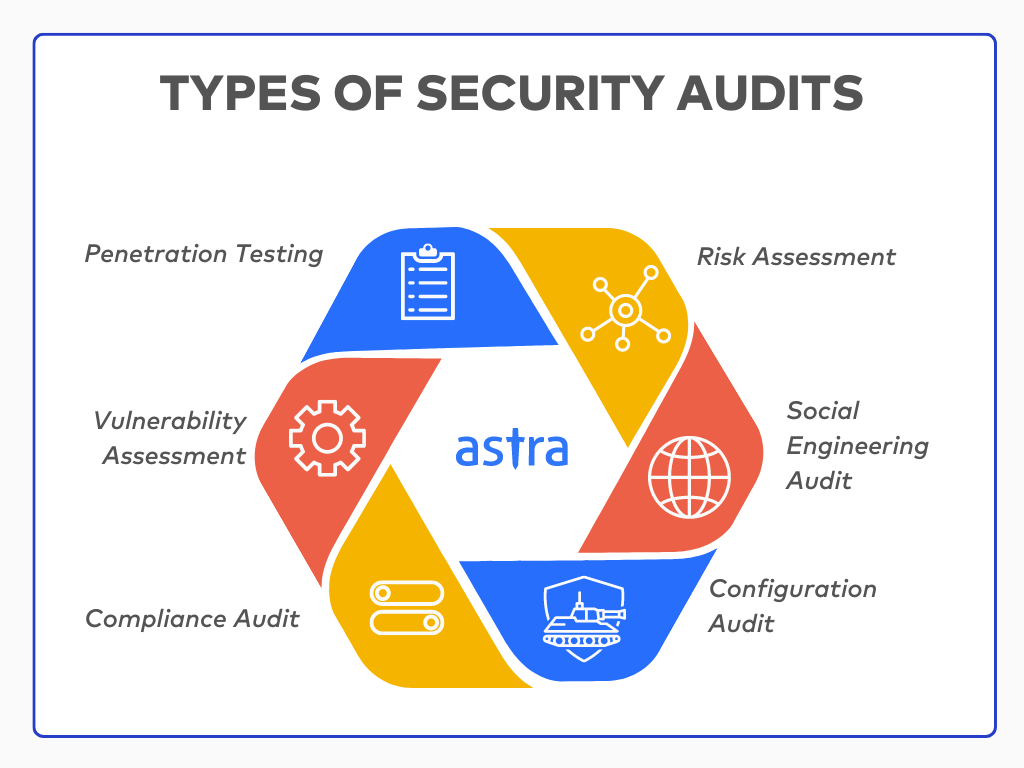
Conducting Security Audits
Regular security audits can help identify weaknesses within an organization’s network and applications. These audits should encompass a thorough review of compliance regulations, potential risks, and security measures employed.
Global Response to Microsoft’s Security Vulnerabilities
Governments and regulatory bodies around the world are increasingly focusing on cybersecurity, with initiatives aimed at improving organizational preparedness. The European Union proposed the General Data Protection Regulation (GDPR), which mandates strict privacy measures that companies, including Microsoft, must adhere to. Similarly, the U.S. government has established new guidelines to help businesses bolster their cybersecurity strategies in light of increasing attacks.
Conclusion
As Microsoft continues to innovate and expand its product offerings, the complexity of its software systems will likely lead to more vulnerabilities. Understanding these flaws and taking proactive measures is essential for all users—from individuals to large enterprises. By maintaining updated software, training employees, implementing MFA, and conducting regular audits, organizations can significantly reduce their risk of falling victim to cyber-attacks.
Call to Action
It is crucial for organizations to stay informed about the latest security vulnerabilities and patches. Following best practices for cybersecurity can enhance their defenses against potential breaches. Given the rising costs associated with data breaches, investing in security is no longer optional; it is a necessity for protecting sensitive information and maintaining trust with customers and stakeholders.
For ongoing updates and information, organizations can subscribe to Microsoft’s security update blog, which offers insights into patches, vulnerabilities, and best practices for securing their systems.